Today’s #MicrosoftQuickFix is that Microsoft has enabled in Microsoft Defender for Office 365 intra-organizational email protection by default for high-confidence phishing messages containing malicious or spam-based URLs!
This new feature in the Windows Defender for Office 365 Anti-spam policy controls whether spam filtering and the corresponding selected action for the spam verdict is applied to internal messages (email sent between users in your Exchange Online organization).
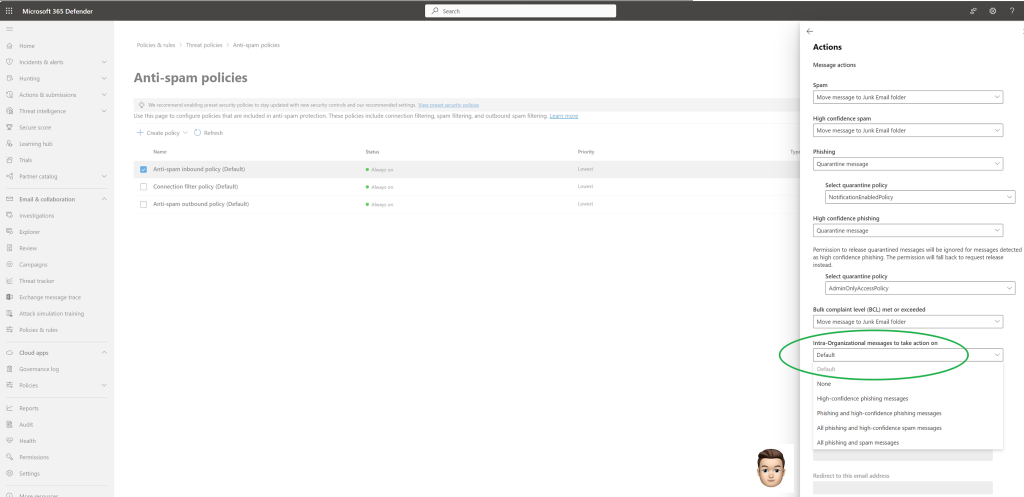
The deployment of this feature is complete for intra-organizational messages with the default value of High confidence phishing messages selected which will quarantine the message. This feature is available in all Microsoft Tenants worldwide!
If you don’t want to utilize this feature on intra-organizational messages it can be disabled by modifying the Anti-spam Policy setting for ‘Intra-Organizational messages to take action on’ to none.
You can also modify the Anti-spam Policy setting to apply to other spam filter verdicts.
For more information about this see:
#Microsoft #Microsoft365 #MicrosoftDefender #ExchangeOnline #MicrosoftCloudSecurity #MicrosoftCloudQuickFix
