I’m back from winter break and today’s #MicrosoftCloudQuickFix is #Microsoft365 finally supports concurrent Exchange Online License Assignments!!! This is going to dramatically reduce the administrative burden managing #ExchangeOnline license assignments and specifically will allow an intuitive groups-based licensing strategy!
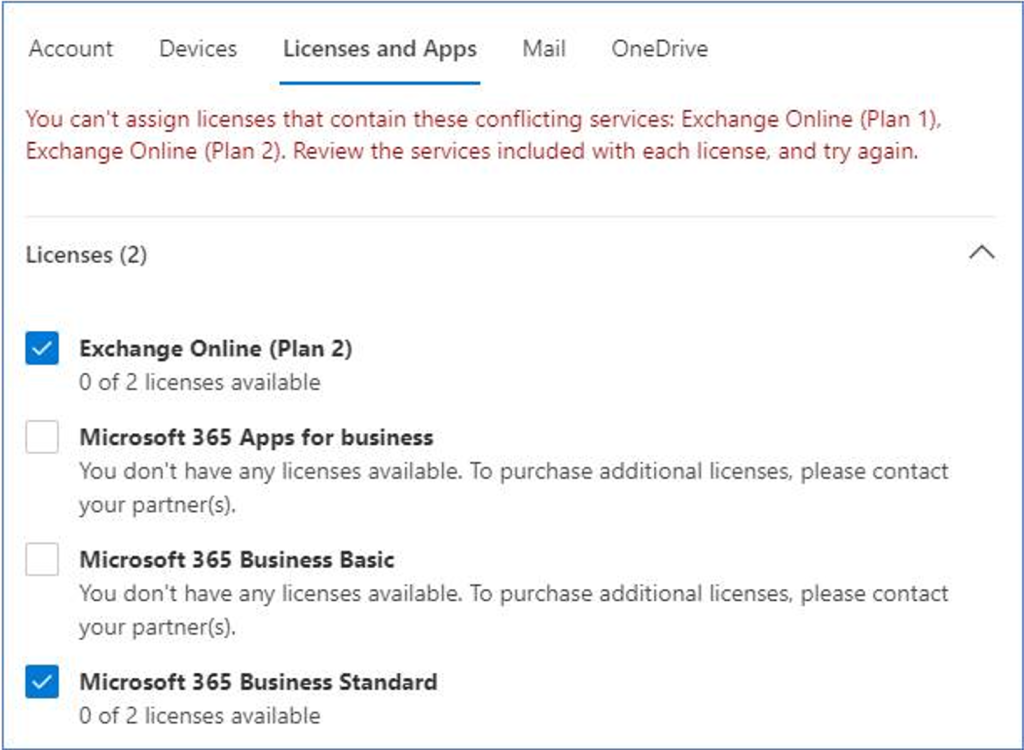
Previously when Microsoft 365 Tenant Admins tried to assign more then one license pack containing #ExchangeOnline to the same user, whether that be thru the Microsoft 365 Admin Center, #AzureActiveDirectory PowerShell, or group-based licensing, an exception message would be displayed and the assignment rejected.
In this case the user already has an Exchange Online Plan 1 license included in Microsoft 365 Business Standard suite and the Tenant Admin is looking to upgrade the user to an Exchange Online Plan 2 license likely to take advantage of the larger mailbox size, Data Loss Prevention, In-place Hold, or Exchange Online Archiving capabilities.
The same exception message is displayed for any combination of the following licenses:
- Microsoft 365 Business packages: Basic, Standard, Premium
- Microsoft / Office 365 F1, F2, F3, E1, E3, E5, A1, A3, A5
- Exchange Online Essentials
- Exchange Online Kiosk
- Exchange Online Plan 1
- Exchange Online Plan 2
- Other #MicrosoftTeams and #MicrosoftProject license packs which rely on Exchange Online
Now with this change any combination of the above is allowed and Exchange Online will automatically decide which of the assigned plans is “superior” and will enable the features of that plan (mailbox quotas, transport limits, protocol access, etc.).
When a license is removed Exchange Online will reevaluate and adjust as needed to the new superior plan.
For more information, please see the following Exchange Team Blog post.
#MicrosoftCloudQuickFix #Microsoft365 #AzureActiveDirectory #ExchangeOnline