So you have done your due diligence and are sure your in the clear. You would like to manage this change and turn off Basic Authentication and test yourself before and not wait for Microsoft. That is todays #MicrosoftCloudQuickFix !
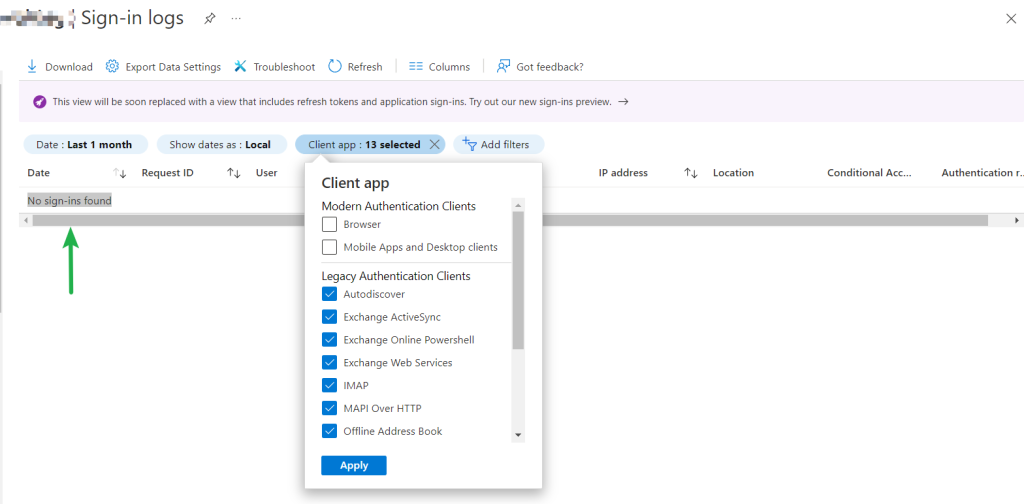
As outlined in my previous blogpost to prepare for the change check the Azure Active Directory Sign-In logs per New tools to block legacy authentication in your organization – Microsoft Tech Community which will help track down any clients still using Basic Authentication.
If you don’t have any Basic Authentication sign-ins then you can move on to block Basic Authentication for protocols on your tenant.
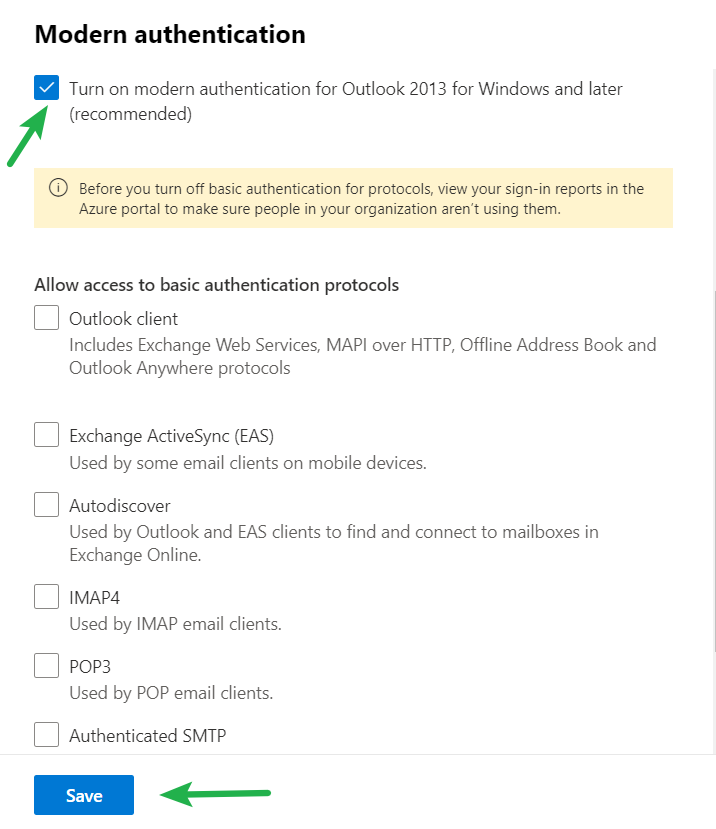
In your Microsoft 365 Admin Portal Next navigate to settings > Org Settings > under Services > Modern Authentication and ensure that “Turn on modern authentication for Outlook 2013 for Windows and later” is enabled and then under “Allow access to basic authentication protocols” uncheck any protocols you wish to no longer use Basic Authentication. Click “Save” and test.
For more information check out the following Disable Basic authentication in Exchange Online | Microsoft Docs in Microsoft Docs.
#Microsoft365 #ExchangeOnline #BasicAuthentication #ModernAuthentication #MicrosoftCloudSecurity #MicrosoftCloudQuickFix